1 Overview
To limit the impacts of a ransomware attack, a complete ransomware protection system is needed. This includes enhancing the network protection features to reduce system vulnerabilities, thus lowering the likelihood of a successful attack; improving the security and resilience of core data, to both prevent data encryption and provide quick detection and alarm in the event the network layer defenses fail; and retaining a complete clean copy of data for recovery purposes, and reducing any losses in case the production data or even the entire data center is encrypted.
1.1 Network, Endpoint, and Storage: A Layered Defense Approach
As a typical ransomware intrusion can be divided into four stages (sniffing, intrusion, diffusion, and extortion), comprehensive protection should be built on pre-event defense, in-event blocking, and post-event recovery. Northrop Grumman’s Defense in Depth framework offers a security architecture over five layers to protect the network and related data. These security layers – perimeter, network, endpoint, application, and data – where the network and application layers run to prevent ransomware attacks in the sniffing, intrusion, and diffusion stages. In the event a ransomware virus reaches the data layer, storage is considered the last line of defense to ensure the confidentiality and authenticity of your data.
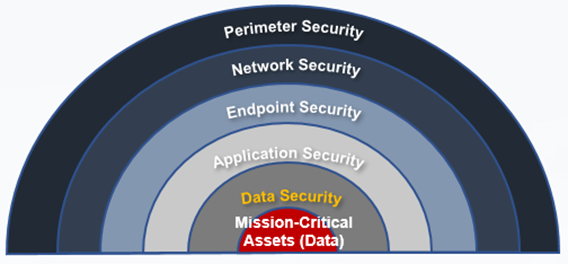
Figure 5: Northrop Grumman Defense-in-Depth (DiD) model
1.1.1 The Network Layer
Protection at this layer runs perimeter and network security methods like firewalls, which prevent ransomware intrusion and block the spread of known threats. In addition, strict network security policies are simple-yet-effective measures to defend against system attacks. Practices like limiting external access to your system, securing high-risk ports (such as ports 139 and 445), enabling file filtering for high-risk files, or using URL filtering to block malicious websites will help avoid unintentional download of malicious code, while other high-security measures to include sandbox, deception system, and comprehensive detection system.
1.1.2 The Endpoint Layer
Security protection over the endpoint and application is built at the endpoint layer. The protection is ensured by using access control, security patches, security audit, and antivirus software technologies, which aim to prevent ransomware from gaining a foothold in the system. Enterprises need to provide regular information security trainings for employees, to prevent attackers from stealing sensitive information through social engineering methods, in addition to conducting better enterprise-wide security governance and host security. Main security measures include securing any system vulnerabilities, upgrading security patches and virus libraries to identify and remove viruses before they strike, and periodical backup of data to enable instant business recovery.
The combination of the network- and endpoint-layer protection helps contain the horizontal spread of viruses to a confined area. In isolation, however, these are insufficient. Because ransomware disguises its malware, and is recorded as trustworthy by the system, so by the time you are aware of an attack, the damage is already done – ransomware has already found and isolated your high-value data, including the backup data of the entire network environment, targeting the backup system and related data specifically, to make it impossible to use backups to restore systems.
1.1.3 The Storage Layer
Protection at the storage layer is used to supplement the traditional ransomware protection solution, which comprises only protection measures at the network and endpoint layers. Modern storage is able to both detect abnormal I/Os and perceive the data changes created by the encryption behavior, before flagging the intrusion of ransomware to the anti-tamper technologies, which prevent the virus from spreading. These technologies also work with the backup storage and the isolation-zone storage to quickly stop the losses caused by ransomware. In addition, offline copies stored in the isolation zone ensure a clean and uninfected data copy is always available for service recovery, and to quickly stop the loss caused by ransomware.
1.2 Storage: The Last Line of Defense for Data Security
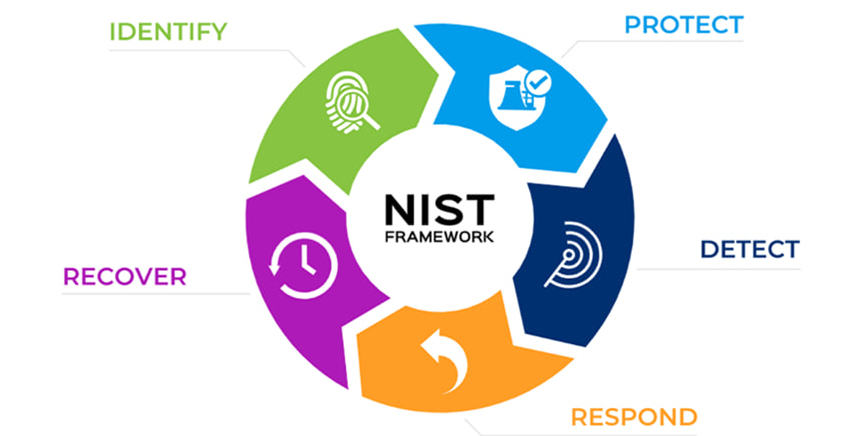
The National Institute of Standards and Technology (NIST) released the Cybersecurity Framework (CSF), which provides guidance on assessing and improving organization-wide capabilities to better prevent, detect, respond to cyber incidents. The framework uses business drivers to guide cybersecurity activities and views cybersecurity as part of the enterprise risk management process. According to the SANS 2019 State of OT/ICS Cybersecurity Survey, the NIST CSF is one of the most widely used security frameworks by organizations to help manage cybersecurity risks.
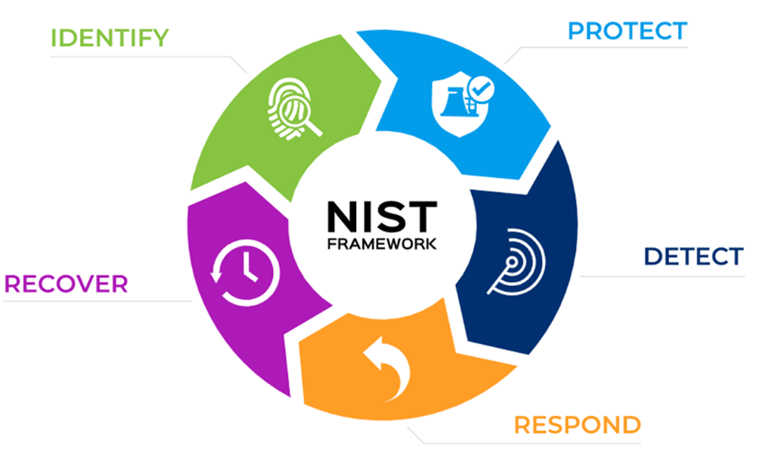
Figure 6: NIST CSF
The five core functions of the NIST CSF provide a strategic view of the lifecycle of cybersecurity risk management and should be considered as key references. Ransomware protection at the storage layer also needs to comply with NIST’s five-step cybersecurity suggestions:
- Identify
- Organizations must understand their environments, identify and prioritize data assets, and manage cybersecurity risks to systems, assets, data, and capabilities.
- Protect
- Develop and implement appropriate safeguards to limit or alleviate the impact of potential cybersecurity incidents. For example, use secure snapshots and WORM file systems to prevent unauthorized data changes, even if permissions are stolen during the protection period; use encryption to prevent data leakage at the network and storage layers; and use the air gap technology to build an isolation zone for offline data protection to prevent data from being attacked and stolen.
- Detect
- Develop all-round detection capabilities to quickly identify cybersecurity incidents. For example, use storage systems’ real-time detection and analysis functions to promptly discover ransomware’s encryption behavior during data read/write, thereby preventing data tampering.
- Respond
- Develop the ability to control the impact of a detected cybersecurity incident. Upon detecting ransomware attacks, your systems must be able to intercept them, proactively protect data, and send alarms. For example, use storage systems’ proactive protection functions, so that secure snapshots are proactively created upon detecting a ransomware attack, thereby minimizing data loss.
- Recover
- Develop and implement appropriate activities to recover any functions or services that are compromised as a result of a cybersecurity incident. For example, if data has been corrupted, select the latest secure data copy, such as a secure snapshot copy or files stored in a WORM file system, to restore data as soon as possible. If the production center has been attacked, use the backup storage for recovery. If the backup storage has also been attacked, restore data from the physically isolated zone.
Implementing the NIST CSF helps organizations focus more on protecting their critical assets, while defending against and reducing losses from ransomware attacks.
Next Volume:Storage-Layer Ransomware Protection Strategy