1 Storage-Layer Ransomware Protection Strategies
To better cope with ransomware attacks, a data security team should establish a comprehensive data protection system, considering both network and storage security. At the data storage layer, the 3-2-1-1 strategy is strongly recommended.
1.1 The 3-2-1-1 Strategy
The 3-2-1 strategy has long been a mainstream guideline for data backup deployments in commercial organizations. To upgrade data security protection, Huawei recommends its enhanced version — the 3-2-1-1 strategy.
The meaning of the strategy is as follows:
- 3: Store 3 copies of data — 1 original plus 2 backups.
- 2: Store data on at least 2 types of storage media.
- 1: Retain 1 remote data copy.
- 1: Retain an extra 1 copy in an air-gap isolation zone.
The purpose of the 3-2-1-1 strategy is to retain the last copy of clean data for rapid recovery after data is damaged by a ransomware attack.
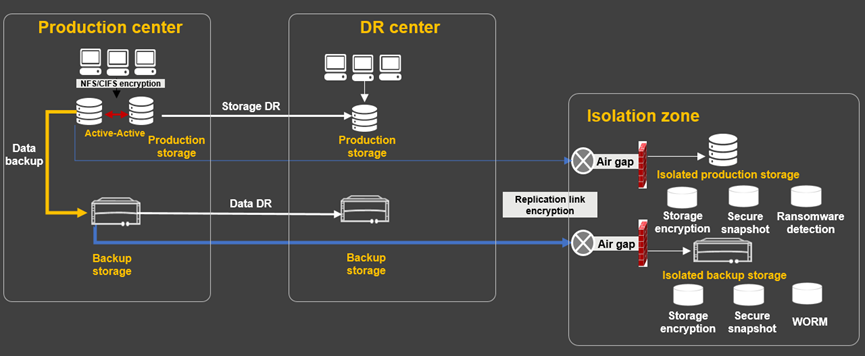
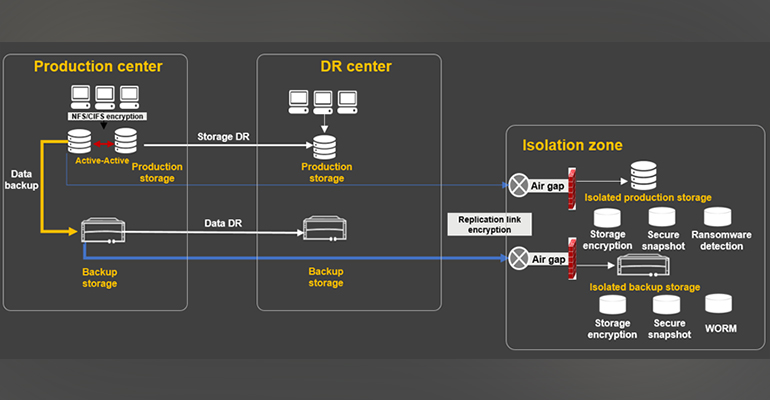
Figure 7: 3-2-1-1 strategy
Why is an isolation zone so important?
There are three reasons:
- A ransomware attack may delete all valid copies of data. The isolation zone uses the air-gap technology to protect data.
- When data does not need to be replicated, the isolation zone is completely offline. As a result, ransomware cannot detect data in the isolation zone, minimizing the possibility of malicious data encryption or deletion.
- When data needs to be replicated, the storage device in the isolation zone only enables the replication ports and only allows one-way data replication, thereby ensuring data security.
- Risks do not just come from the outside. People inside an organization may also be a contributing factor to data loss. Analyst firms say that over the next 3 years, most cyber threats are likely to arise internally. However, the isolation zone is invisible on the network and is managed only by dedicated personnel, meaning it is unlikely to be exposed to or attacked by internal members of staff.
- The isolation zone ensures faster data recovery after ransomware attacks. Although traditional tape libraries can store data offline, their recovery speeds are inadequate. By contrast, both production and backup storage products have evolved to the all-flash architecture, with recovery speeds 100 times faster than tape libraries. This minimizes the service recovery period to reduce the loss caused by service downtime in a ransomware attack.
- Risks do not just come from the outside. People inside an organization may also be a contributing factor to data loss. Analyst firms say that over the next 3 years, most cyber threats are likely to arise internally. However, the isolation zone is invisible on the network and is managed only by dedicated personnel, meaning it is unlikely to be exposed to or attacked by internal members of staff.
1.2 Strategies for Deploying Storage-Layer Ransomware Protection
Full ransomware protection at the storage layer covers the production storage, backup storage, production storage isolation zone, and backup storage isolation zone. In actual construction, enterprises should select appropriate strategies that suit their application needs to build an effective line of defense at the storage layer against ransomware attacks.
The best practice is to back up all data, implement disaster recovery for important systems, and build ransomware protection for core systems.
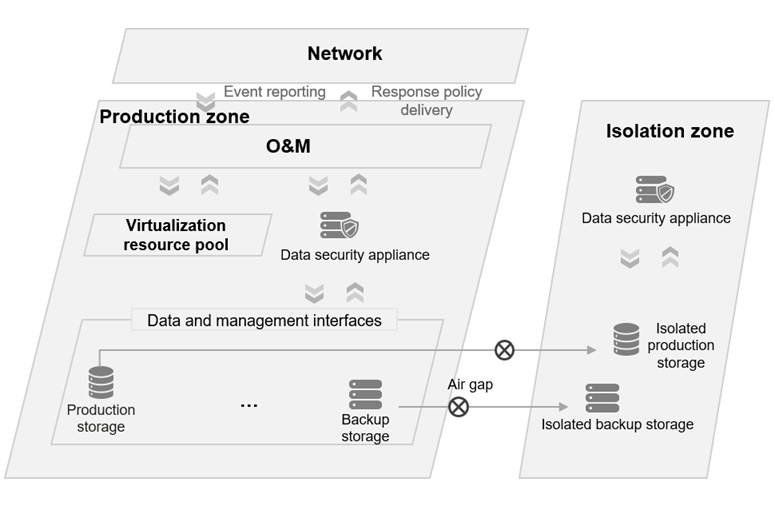
Figure 8: Overview of storage-layer ransomware protection
1.2.1 Use Production Storage to Protect Online Transaction and Manufacturing Systems
If these systems are attacked by ransomware, serious consequences may occur, such as service interruption and production line shutdown. Longer downtime will cause greater losses, in addition to reputational damage to the enterprises. Therefore, enterprises must prioritize rapid service recovery and security level improvement when designing their ransomware protection plans. To meet these goals, enterprises must minimize the recovery point objective (RPO) and ensure that the restored data is nearest to the production storage. It is recommended that enterprises build ransomware protection capabilities on the production storage. Moreover, to implement higher-level security protection and prevent attacks on production storage from causing data loss, it is necessary to build an isolation zone for the production storage. This not only takes security protection to the next level, but also retains data for a longer period of time to cope with latent ransomware threats.
- Enable the ransomware detection function on the production storage and isolated production storage to ensure that ransomware attacks can be detected and prevented promptly. If a high-end storage device is used, which offers a surplus of performance, it is recommended that enterprises use its built-in ransomware detection function to simplify system deployment. If there is no surplus of storage performance or multiple storage devices are deployed, it is better to use a data security appliance to implement unified management and improve detection performance. In addition to significant advantages in their resistance to attacks, dedicated devices focus on individual functions to deliver better stability. Typically, ransomware detection in the data write stage includes pre-event interception, in-event real-time detection, and post-event comprehensive scanning.
- Enable anti-tampering functions, such as secure snapshot, on the production storage and isolated storage. To achieve the service level agreement (SLA) and optimal cost-effectiveness of applications, set the creation frequency and retention time for secure snapshots based on the following rule: The closer a storage system to the production data, the more frequent creation and shorter retention of secure snapshots. For example, if the recovery period designed for an application is shorter than 2 hours, you are advised to set the creation frequency to be shorter than 2 hours and the retention time to 1 to 3 days for secure snapshots on the production storage. Data must be periodically replicated from the production storage to the isolated production storage. The recommended cycle is every 12 to 24 hours. The frequency for creating secure snapshots on the isolated production storage should be the same as the replication cycle, and the retention time is typically 7 to 30 days.
- Enable data encryption. If IP links are used to transmit data between the production storage and the isolated production storage, link encryption is recommended to prevent data leakage during transmission. If industry regulations require storage devices to encrypt data, storage encryption functionality needs to be planned. Otherwise, enterprises can determine whether to enable storage encryption for preventing storage media theft from data leakage.
- Enable anti-tampering functions, such as secure snapshot, on the production storage and isolated storage. To achieve the service level agreement (SLA) and optimal cost-effectiveness of applications, set the creation frequency and retention time for secure snapshots based on the following rule: The closer a storage system to the production data, the more frequent creation and shorter retention of secure snapshots. For example, if the recovery period designed for an application is shorter than 2 hours, you are advised to set the creation frequency to be shorter than 2 hours and the retention time to 1 to 3 days for secure snapshots on the production storage. Data must be periodically replicated from the production storage to the isolated production storage. The recommended cycle is every 12 to 24 hours. The frequency for creating secure snapshots on the isolated production storage should be the same as the replication cycle, and the retention time is typically 7 to 30 days.
1.2.2 Use Backup Storage to Protect Important Application Systems Served by Different Production Storage Devices
If production storage devices used by an enterprise are from different vendors, unified ransomware protection is required for the application systems running on these storage devices. Because different vendors vary in capabilities, some vendors may not offer ransomware protection. Even if all vendors provide ransomware protection, deploying a ransomware solution for each storage device is too complex and costly. In this case, it is a good practice to build ransomware protection on dedicated backup storage. Similarly, an isolation zone must be established for backup storage to protect data offline, preventing attacks on backup storage from causing data loss. Because backup storage is the last line of defense, it is critical to build a backup isolation zone.
- Use anti-tampering functions such as WORM and secure snapshot to protect data. Backup storage usually works with dedicated backup software to back up application systems’ data as files. If dedicated backup software can implement WORM jointly with backup storage, prefer WORM to prevent data tampering. The WORM technology can protect files separately, which is more flexible and fine-grained. If dedicated backup software cannot work with the WORM file system on the backup storage, you can use the secure snapshot function on the backup storage to prevent data tampering.
- Enable ransomware detection. Backup storage is not used as frequently as production storage. Therefore, enabling ransomware detection on backup storage has a relatively minor impact on application performance. Ransomware detection helps prevent latent viruses from encrypting infrequently used data, so that backup data will remain available. Implementing ransomware detection on backup storage and isolated backup storage ensures that data used for recovery is clean and secure, thus improving recovery efficiency. Ransomware detection on backup storage comes in two forms: built-in function and external data security appliance. You can select one based on your data center needs.
2 Conclusion
Ransomware protection needs to be implemented from three aspects — management system, security policy, and technical capabilities.
First, build a robust defense for basic cybersecurity, such as using firewalls and sandboxes.
Second, build up employees’ security awareness and train employees to develop good working habits and abilities to identify and prevent typical attacks.
Finally, strengthen the last line of defense at the storage layer for ransomware protection. For example, enable detection and analysis to identify ransomware attacks and secure copies in a timely manner, use WORM and secure snapshots to prevent data tampering, use encryption to prevent data leakage, and use air gap to build an isolation zone for offline data protection, thereby retaining the last copy of clean data for recovery.